Overview
Microsoft Windows is vulnerable to remote code execution via an error in handling files using the Windows Metafile image format. Exploit code has been publicly posted and used to successfully attack fully-patched Windows XP SP2 systems. However, other versions of the Windows operating system also may be at risk.
Description
Windows Graphic Display Interface (GDI) Windows GDI is an interface that "enables applications to use graphics and formatted text on both the video display and the printer." GDI functions can be used to draw lines, text, curves, and other graphical elements.
The public exploits currently use the Windows Picture and Fax Viewer (SHIMGVW.DLL) as an attack vector. However, please note that disabling the Windows Picture and Fax Viewer will not eliminate this vulnerability. Limited testing has shown that any application that makes the SetWinMetaFileBits GDI function call may be used to trigger the SETABORTPROC GDI Escape on Windows NT, Windows 2000, Windows XP, and Windows Server 2003. The GDI implementation of Windows 98 and Windows Me appears to be different in that the PlayMetaFile GDI function seems to trigger the SETABORTPROC GDI Escape. Any application that can open a file with the associated program for that file type, such as one that uses ShellExecute, can be used as an attack vector. Most email clients can be used as an attack vector for this vulnerability in this way. Windows Picture and Fax Viewer is the application that is associated with WMF and other graphic files by default on Windows XP and Windows Server 2003. Internet Explorer is a common attack vector for this vulnerability because, in its default configuration, it can automatically launch the Windows Picture and Fax Viewer as the result of viewing a web page. Google Desktop Search (GDS) can also trigger the vulnerability if a malicious WMF file is placed in a location that is indexed. Other content indexing software may also be vulnerable. The following diagram illustrates several attack vectors for this vulnerability: 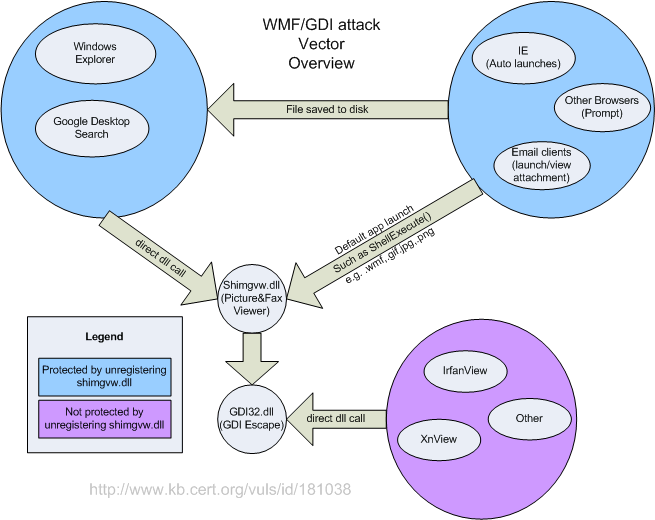 |
Impact
A remote, unauthenticated attacker may be able to execute arbitrary code if the user is persuaded to view a specially crafted Windows Metafile. |
Solution
Apply a patch from your vendor |
To undo this change, re-register Shimgvw.dll by following the above steps. Replace the text in Step 1 with "regsvr32 %windir%\system32\shimgvw.dll" (without the quotation marks). Install an unofficial hotfix Ilfak Guilfanov has provided a hotfix to intercept calls to the Escape function in GDI32.DLL. With this hotfix installed, calls to the obsolete SETABORTPROC GDI Escape will reportedly fail. This appears to prevent exploitation of this vulnerability. Note that this is not an official fix from Microsoft. Please take the appropriate risk assessment steps to determine whether such a hotfix should be installed in your environment. Do not access Windows Metafiles from untrusted sources Exploitation occurs by accessing a specially crafted Windows Metafile. By only accessing Windows Metafiles from trusted or known sources, the chances of exploitation are reduced. Attackers may host malicious Windows Metafiles on web sites. In order to convince users to visit their sites, those attackers often use a variety of techniques to create misleading links including URL encoding, IP address variations, long URLs, and intentional misspellings. Do not click on unsolicited links received in email, instant messages, web forums, or internet relay chat (IRC) channels. Type URLs directly into the browser to avoid these misleading links. While these are generally good security practices, following these behaviors will not prevent exploitation of this vulnerability in all cases, particularly if a trusted site has been compromised or allows cross-site scripting. Please note that Windows Metafile data may be saved with an extension other than WMF. A file with any extension that is associated with Windows Picture and Fax Viewer can be used to exploit this vulnerability. By default, Windows Picture and Fax Viewer is associated with the following file extensions:
By blocking access to Windows Metafiles using HTTP proxies, mail gateways, and other network filter technologies, system administrators may also limit potential attack vectors. Please be aware we have confirmed that filtering based just on the WMF file extensions or MIME type application/x-msMetafile will not block all known attack vectors for this vulnerability. Filter mechanisms should be looking for any file that Microsoft Windows recognizes as a Windows Metafile by virtue of its file header. Please check with your network vendor for updated signatures. WMF files can begin with various byte sequences such as:
02 00 09 00 ... D7 CD C6 9A ... Disabling downloads in the Internet Explorer Internet Zone (or any zone used by an attacker) appears to help prevent exploitation of this vulnerability. This can be achieved by changing the Internet Zone security setting to "High." Instructions for changing zone security settings can be found in the Malicious Web Scripts FAQ. While this change does not remove the vulnerability, it does help to prevent a common attack vector. |
Vendor Information
CVSS Metrics
| Group | Score | Vector |
|---|---|---|
| Base | ||
| Temporal | ||
| Environmental |
References
- http://www.microsoft.com/technet/security/advisory/912840.mspx
- http://support.microsoft.com/kb/81497
- http://blogs.technet.com/msrc/archive/2006/01/13/417431.aspx
- http://www.hexblog.com/2005/12/wmf_vuln.html
- http://support.microsoft.com/kb/84984
- http://msdn.microsoft.com/library/en-us/gdi/prntspol_0d6b.asp
- http://windowssdk.msdn.microsoft.com/library/en-us/gdi/prntspol_9kok.asp
- http://msdn.microsoft.com/library/en-us/gdi/prntspol_0883.asp
- http://msdn.microsoft.com/library/en-us/dnanchor/html/gdi.asp
- http://msdn.microsoft.com/library/en-us/gdi/sec_gdi.asp
- http://msdn.microsoft.com/library/en-us/gdi/metafile_0hmb.asp
- http://msdn.microsoft.com/library/en-us/gdi/metafile_1xwz.asp
- http://isc.sans.org/diary.php?storyid=994
- http://isc.sans.org/diary.php?rss&storyid=972
- http://isc.sans.org/diary.php?storyid=975
- http://secunia.com/advisories/18255/
- http://www.securityfocus.com/bid/16074
- http://vil.mcafeesecurity.com/vil/content/v_137760.htm
- http://www.f-secure.com/weblog/archives/archive-122005.html#00000753
- http://www.symantec.com/avcenter/venc/data/bloodhound.exploit.56.html
- http://www.ciac.org/ciac/bulletins/q-085.shtml
- http://www.juniper.net/security/auto/vulnerabilities/vuln2830.html
- http://www.osvdb.org/displayvuln.php?osvdb_id=21987
- http://xforce.iss.net/xforce/alerts/id/211
- http://securitytracker.com/alerts/2005/Dec/1015416.html
- http://www.sysinternals.com/blog/2006/01/inside-wmf-backdoor.html
Acknowledgements
This document was written by Jeffrey S. Havrilla and Will Dormann.
Other Information
| CVE IDs: | CVE-2005-4560 |
| Severity Metric: | 53.58 |
| Date Public: | 2005-12-27 |
| Date First Published: | 2005-12-28 |
| Date Last Updated: | 2006-01-20 20:18 UTC |
| Document Revision: | 101 |