Overview
ReadyNet WRT300N-DD Wireless Router, firmware version 1.0.26, uses default credentials, is vulnerable to cross-site request forgery, and uses insufficiently random values for DNS queries.
Description
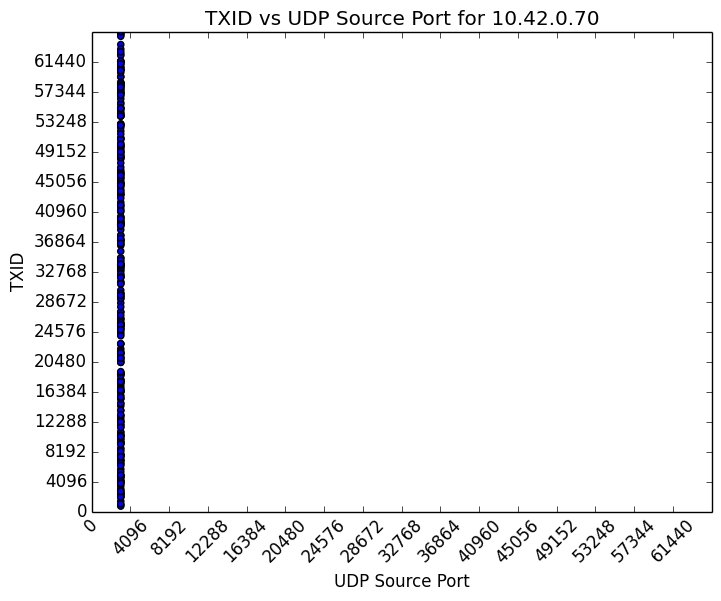
CWE-255: Credentials Management - CVE-2015-7280 The ReadyNet WRT300N-DD Wireless Router web administration interface uses non-random default credentials of admin:admin. A local area network attacker can gain privileged access to a vulnerable device's web management interfaces or leverage default credentials in remote attacks such as cross-site request forgery. |
Impact
A remote, unauthenticated attacker may be able to spoof DNS responses to cause WRT300N-DD LAN clients to contact attacker-controlled hosts or induce an authenticated user into making an unintentional request to the web server that will be treated as an authentic request. A local area network attacker can take complete control of a device using default admin credentials. |
Solution
The CERT/CC is currently unaware of a practical solution to this problem. Until these vulnerabilities are addressed, users should consider the following workarounds. |
Restrict access and use strong passwords |
Vendor Information
CVSS Metrics
| Group | Score | Vector |
|---|---|---|
| Base | 6.8 | AV:N/AC:M/Au:N/C:P/I:P/A:P |
| Temporal | 6.5 | E:F/RL:U/RC:C |
| Environmental | 1.6 | CDP:ND/TD:L/CR:ND/IR:ND/AR:ND |
References
Acknowledgements
These vulnerabilities were reported by Joel Land of the CERT/CC.
This document was written by Joel Land.
Other Information
| CVE IDs: | CVE-2015-7280, CVE-2015-7281, CVE-2015-7282 |
| Date Public: | 2015-12-10 |
| Date First Published: | 2015-12-10 |
| Date Last Updated: | 2015-12-10 17:04 UTC |
| Document Revision: | 18 |