Overview
Microsoft Windows Remote Desktop Gateway contains vulnerabilities that may allow a remote, unauthenticated attacker to execute arbitrary code with SYSTEM privileges on a vulnerable system.
Description
Microsoft Windows Remote Desktop Gateway (RD Gateway) is a Windows Server component that provides access to Remote Desktop services without requiring the client system to be present on the same network as the target system. Originally launched as Terminal Services Gateway (TS Gateway) with Windows Server 2008, RD Gateway is a recommended way to provide Remote Desktop connectivity to cloud-based systems. For example, guidance has been provided for using RD Gateway with AWS, and also with Azure. The use of RD Gateway is recommended to reduce the attack surface of Windows-based hosts. Microsoft RD Gateway in Windows Server 2012 and later contain two vulnerabilities that can allow an unauthenticated remote attacker to execute arbitrary code with SYSTEM privileges. It is reported by Kryptos Logic that the flaws lie in handling of fragmentation. This vulnerability is exploitable by connecting to the RD Gateway service listening on UDP/3391. |
Impact
By sending a specially-crafted request to a Remote Desktop Gateway server, an unauthenticated remote attacker to execute arbitrary code with SYSTEM privileges. |
Solution
Apply an update |
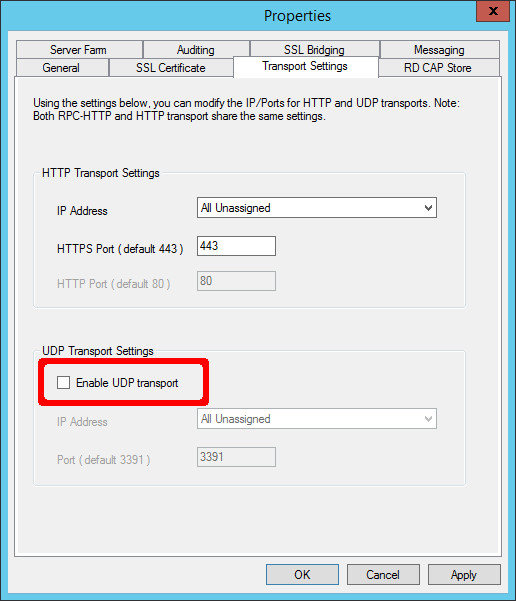
Disable Remote Desktop Gateway UDP transport |
Vendor Information
CVSS Metrics
| Group | Score | Vector |
|---|---|---|
| Base | 10 | AV:N/AC:L/Au:N/C:C/I:C/A:C |
| Temporal | 7.8 | E:POC/RL:OF/RC:C |
| Environmental | 5.9 | CDP:ND/TD:M/CR:ND/IR:ND/AR:ND |
References
- https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2020-0609
- https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2020-0610
- https://docs.microsoft.com/en-us/windows-server/remote/remote-desktop-services/rds-roles#remote-desktop-gateway
- https://aws.amazon.com/quickstart/architecture/rd-gateway/
- https://docs.microsoft.com/en-us/azure/active-directory/manage-apps/application-proxy-integrate-with-remote-desktop-services
- https://docs.microsoft.com/en-us/openspecs/windows_protocols/ms-tsgu/0007d661-a86d-4e8f-89f7-7f77f8824188
- https://techcommunity.microsoft.com/t5/ask-the-performance-team/ws2008-terminal-services-gateway-overview/ba-p/372882
- https://www.kryptoslogic.com/blog/2020/01/rdp-to-rce-when-fragmentation-goes-wrong/
Acknowledgements
This document was written by Will Dormann.
Other Information
| CVE IDs: | CVE-2020-0609, CVE-2020-0610 |
| Date Public: | 2020-01-14 |
| Date First Published: | 2020-01-14 |
| Date Last Updated: | 2020-01-18 14:55 UTC |
| Document Revision: | 41 |