Overview
Microsoft Windows RDP can allow an attacker to bypass the lock screen on remote sessions.
Description
In Windows a session can be locked, which presents the user with a screen that requires authentication to continue using the session. Session locking can happen over RDP in the same way that a local session can be locked. CWE-288: Authentication Bypass Using an Alternate Path or Channel (CVE-2019-9510)
At this point, an attacker can interrupt the network connectivity of the RDP client system. The RDP client software will automatically reconnect to the remote system once internet connectivity is restored. But because of this vulnerability, the reconnected RDP session is restored to a logged-in desktop rather than the login screen. This means that the remote system unlocks without requiring any credentials to be manually entered. Two-factor authentication systems that integrate with the Windows login screen, such as Duo Security MFA, may also bypassed using this mechanism. We suspect that other MFA solutions that leverage the Windows login screen are similarly affected. Any login banners enforced by an organization will also be bypassed. It is important to note that this vulnerability is with the Microsoft Windows lock screen's behavior when RDP is being used, and the vulnerability is present when no MFA solutions are installed. While MFA product vendors are affected by this vulnerability, the MFA software vendors are not necessarily at fault for relying on the Windows lock screen to behave as expected. Note that this vulnerability was originally described as requiring Network Level Authentication (NLA). We have since confirmed that this behavior is present whether or not NLA is enabled. Also, some combinations of RDP clients and Windows versions prior to Windows 10 1803 and Server 2019 may also demonstrate automatic session unlocking upon RDP reconnect. In such cases, neither MFA integrated with the login screen nor login banner displaying is bypassed in our testing. Although these cases are a different issue than VU#576688, the workarounds listed in this vulnerability note should still be applied to prevent these similar symptoms. |
Impact
By interrupting network connectivity of a system, an attacker with access to a system being used as a Windows RDP client can gain access to a connected remote system, regardless of whether or not the remote system was locked. |
Solution
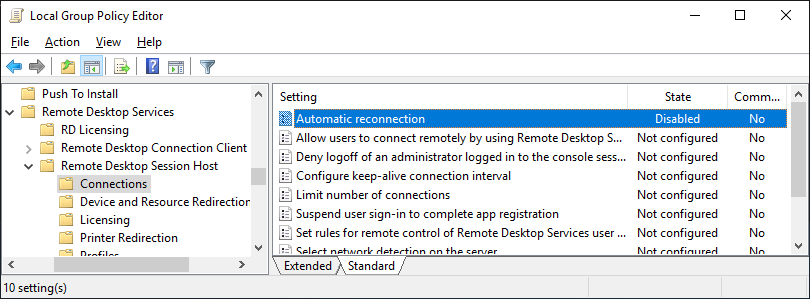
The CERT/CC is currently unaware of a practical solution to this problem. Please consider the following workarounds. |
Disable RDP Automatic Reconnection on RDP servers |
Vendor Information
Note that vendors other than Microsoft listed as "Affected" are simply indicators that the vendors have products that are affected by this vulnerability in Microsoft Windows RDP. The vendors' actual products do not necessarily contain a vulnerability, but rather that the vendor has a product that may not provide the login protection as expected, as the result of this issue with Microsoft Windows. |
CVSS Metrics
| Group | Score | Vector |
|---|---|---|
| Base | 4.6 | AV:L/AC:L/Au:N/C:P/I:P/A:P |
| Temporal | 4.1 | E:POC/RL:U/RC:C |
| Environmental | 4.2 | CDP:ND/TD:H/CR:ND/IR:ND/AR:ND |
References
- https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2008-R2-and-2008/cc732713(v=ws.11)
- https://docs.microsoft.com/en-us/openspecs/windows_protocols/ms-rdpbcgr/e729948a-3f4e-4568-9aef-d355e30b5389
- https://social.technet.microsoft.com/Forums/windowsserver/en-US/1fd171de-a1b5-4721-86bf-082e4a375049/rds-2019-but-probably-other-versions-as-well-locked-rdp-session-logs-in-after-session-reconnect
Acknowledgements
Thanks to Joe Tammariello of the SEI for reporting this vulnerability.
This document was written by Will Dormann.
Other Information
| CVE IDs: | CVE-2019-9510 |
| Date Public: | 2019-02-19 |
| Date First Published: | 2019-06-04 |
| Date Last Updated: | 2019-06-19 02:24 UTC |
| Document Revision: | 136 |