Overview
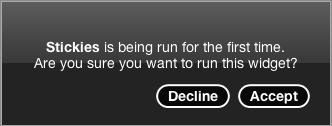
Apple Safari on Mac OS X Tiger automatically installs Dashboard widgets without user intervention or notice.
Description
Dashboard Dashboard is a new feature introduced in Apple Mac OS X Tiger 10.4. Dashboard is a collection of applications called "widgets." The system-installed widgets are located in /Library/Widgets and user-installed widgets are located in ~/Library/Widgets. |
Impact
An attacker may be able to install arbitrary code on a vulnerable system. Since OS X executes user-installed widgets over system-installed widgets with the same bundle identifier (VU#983429), a user may be more likely to unknowingly execute the code. |
Solution
Upgrade or patch |
Vendor Information
CVSS Metrics
| Group | Score | Vector |
|---|---|---|
| Base | ||
| Temporal | ||
| Environmental |
References
- http://www.macworld.com/news/2005/05/09/dashboard/
- http://www.macworld.co.uk/news/index.cfm?home&NewsID=11531
- http://www1.cs.columbia.edu/~aaron/files/widgets/
- http://developer.apple.com/documentation/AppleApplications/Conceptual/Dashboard_Tutorial/index.html
- [<a href="http://developer.apple.com/documentation/AppleApplications/Conceptual/Dashboard_Tutorial/Security/chapter_10_section_1.html#//apple_ref/doc/uid/TP40001340-CH210-TPXREF101">http://developer.apple.com/documentation/AppleApplications/Conceptual/Dashboard_Tutorial/ Security/chapter_10_section_1.html#//apple_ref/doc/uid/TP40001340-CH210-TPXREF101</a>]
- http://www.apple.com/macosx/features/dashboard/
- http://www.appleinsider.com/article.php?id=1073
- http://securitytracker.com/alerts/2005/May/1014012.html
- http://www.securityfocus.com/bid/13694
- http://docs.info.apple.com/article.html?artnum=301630
Acknowledgements
This vulnerability was publicly reported by stephan.com.
This document was written by Will Dormann.
Other Information
| CVE IDs: | CVE-2005-1474 |
| Severity Metric: | 17.06 |
| Date Public: | 2005-05-08 |
| Date First Published: | 2005-06-08 |
| Date Last Updated: | 2006-02-22 15:22 UTC |
| Document Revision: | 27 |