Overview
Several models of ZyXEL routers are vulnerable to multiple issues, including weak default passwords, command injections due to improper input validation, and cross-site scripting.
Description
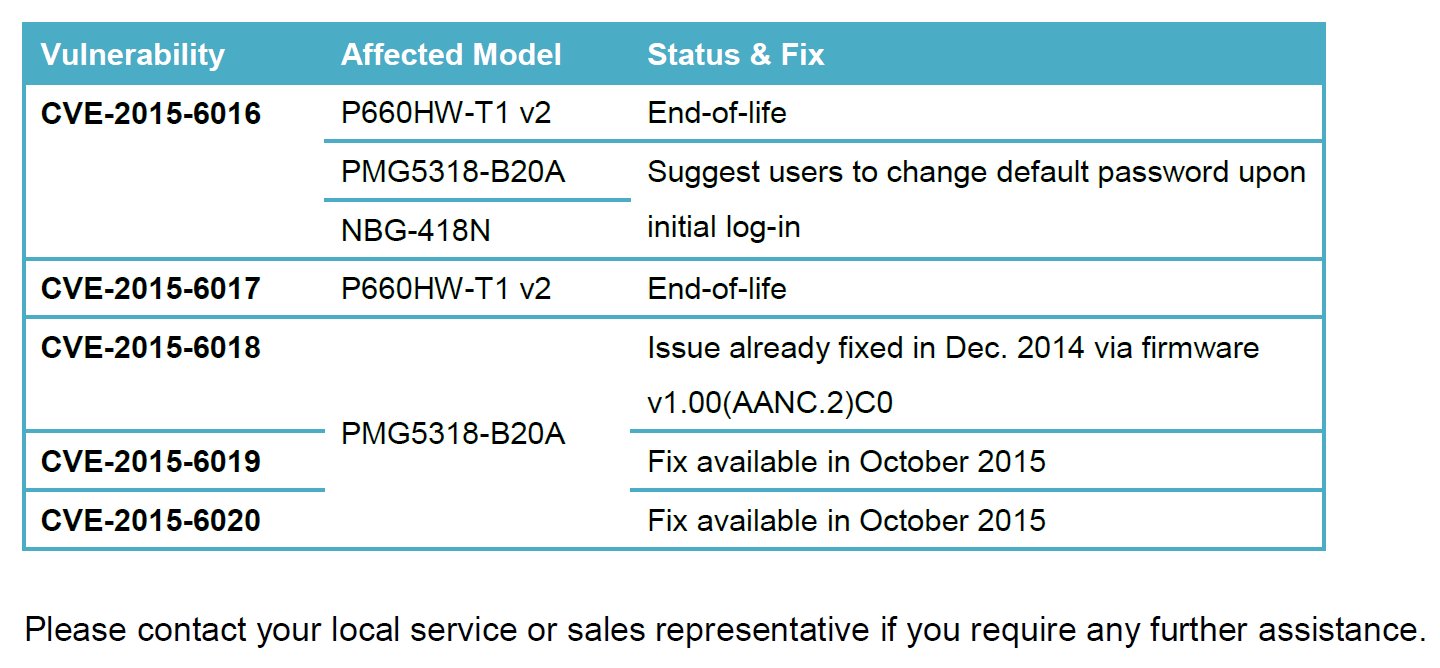
CWE-255: Credentials Management - CVE-2015-6016 According to the reporter, the following models contain the weak default password of "1234" for the admin account:
Many more models have been reported to share this same password. CWE-80: Improper Neutralization of Script-Related HTML Tags in a Web Page (Basic XSS) - CVE-2015-6017 According to the reporter, a reflected cross site scripting vulnerability exists in the LoginPassword and hiddenPassword parameters of the /Forms/rpAuth_1 page on the ZyXEL P-660HW-T1 v2 with ZyNOS firmware version: V3.40(AXH.0) (dated 3/30/2007). CWE-20: Improper Input Validation - CVE-2015-6018 According to the reporter, the diagnostic ping function's PingIPAddr parameter in the ZyXEL PMG5318-B20A, firmware version V100AANC0b5, does not properly validate user input. An attacker may be able to execute arbitrary commands as root. CWE-613: Insufficient Session Expiration - CVE-2015-6019 According to the reporter, the ZyXEL PMG5318-B20A, firmware version V100AANC0b5 does not properly expire the session when a user logs out of the management portal. The reporter has confirmed the session remains active for at least 1 hour after log off. An attacker may be able to utilize session information to gain access to the device even after the user has logged off. CWE-285: Improper Authorization - CVE-2015-6020 According to the reporter, the regular user account on the ZyXEL PMG5318-B20A, firmware version V100AANC0b5 has full administrative access, rather than restricted access. |
Impact
A remote unauthenticated attacker may be able to modify system configuration. |
Solution
Apply updates and other changes |
Vendor Information
CVSS Metrics
| Group | Score | Vector |
|---|---|---|
| Base | 8.3 | AV:A/AC:L/Au:N/C:C/I:C/A:C |
| Temporal | 7.1 | E:POC/RL:U/RC:UR |
| Environmental | 5.3 | CDP:ND/TD:M/CR:ND/IR:ND/AR:ND |
References
Acknowledgements
Thanks to Joel Land for reporting the vulnerability in the NBG-418N. Thanks to Karn Ganeshen for reporting the remaining vulnerabilities to us.
This document was written by Garret Wassermann.
Other Information
| CVE IDs: | CVE-2015-6016, CVE-2015-6017, CVE-2015-6018, CVE-2015-6019, CVE-2015-6020 |
| Date Public: | 2015-10-13 |
| Date First Published: | 2015-10-13 |
| Date Last Updated: | 2015-10-29 13:38 UTC |
| Document Revision: | 45 |